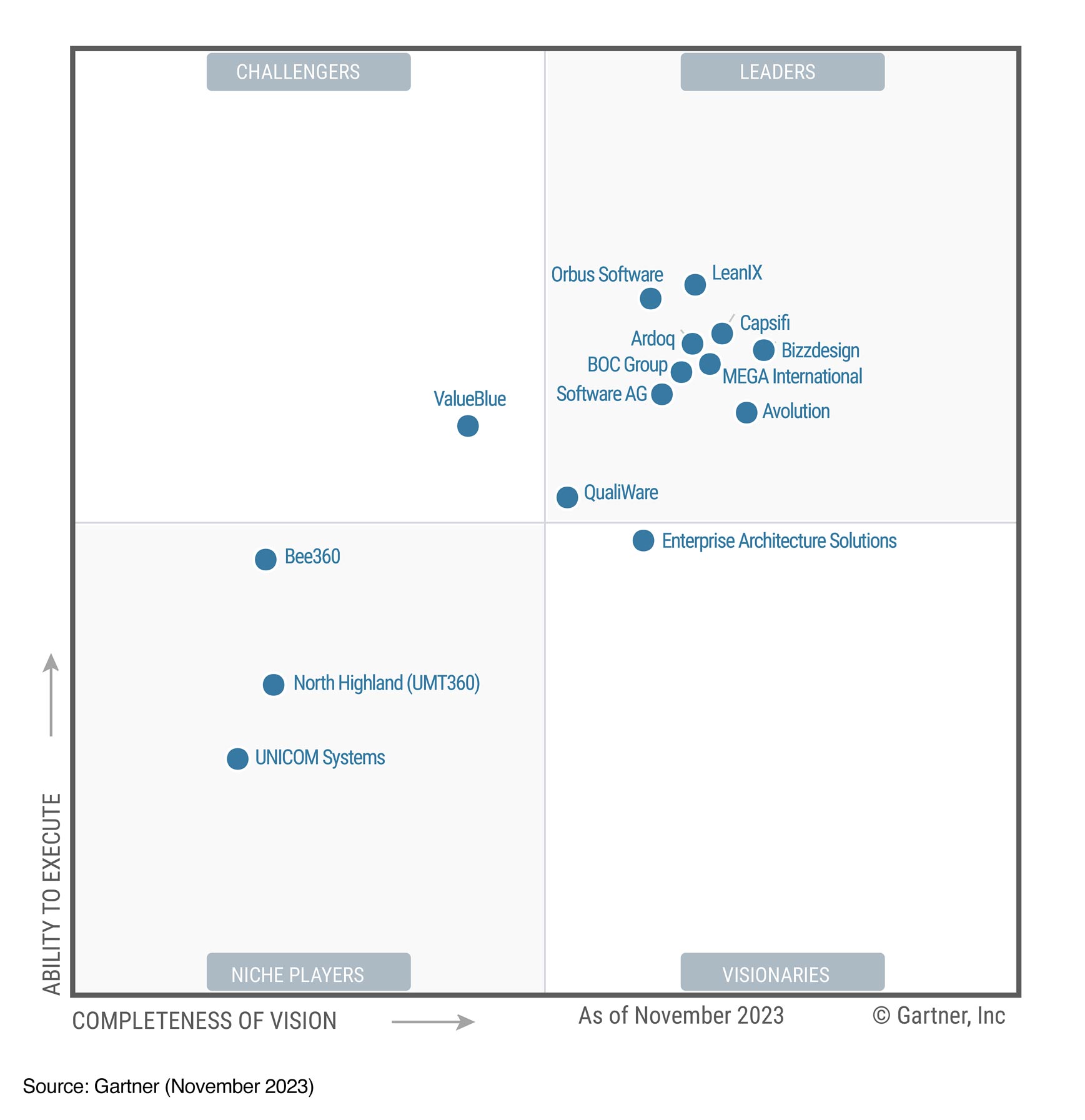
2023 Gartner® Magic Quadrant™
for Enterprise Architecture Tools
Bizzdesign named a Leader for the 8th consecutive year and positioned highest for Completeness of Vision
Change by Design
See the full picture.
Find the right path.
Execute with confidence.
Our enterprise architecture software helps organizations dramatically increase the success rate of enterprise transformation, strategic investment allocation and risk management.