To be in control of the risks you run, the first thing you need is a strategic insight into your organization from a security risk management perspective. This requires a consistent and up-to-date overview of your current landscape of products, processes, applications, infrastructure, and all related risk & security aspects. C-level management cannot fulfill its responsibilities without knowing the main risk-related issues.
Having an understanding of these relationships also helps you to assess the effects of business decisions. This provides the business with a clear insight into the enterprise risks related to, for example, introducing new products and initiatives, outsourcing business processes or IT systems, or assimilating another organization after a merger. Thus, they can weigh the risk propensity of the enterprise against the potential consequences.
Moreover, the propagation of risks throughout the enterprise is of great concern to executives and operational management. Risks in one area may entail risks in another. For example, what are the potential ripple effects of a system failure, break-in, power outage, fraud or other mishap on critical business processes, services, clients, partners, markets…? Enterprise architecture helps you to create insight into these relations and dependencies, and thus avoid or mitigate potential disasters.
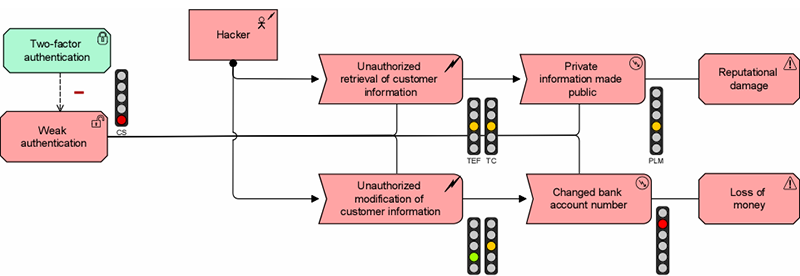
A related area in which enterprise architecture provides tangible business value is in aligning security and risk management with business goals and objectives. Many organizations find it difficult to decide on the right level of security measures, and business managers often see this as a technical issue that is left to the IT people. They, in turn, don’t want to take any risks and create gold-plated, secure solutions but also very expensive (and often rather unfriendly towards users).
Better alignment between business goals, architectural decisions and technical implementation helps the organization to spend its security budget wisely, focused on business-relevant risks. This may lead to both cost savings and lower risks, because you are not investing in overly strong security measures for unimportant stuff, leaving more budget to protect the things your enterprise really cares about.
ALSO READ: Choosing the right enterprise architecture tool for Security Risk Management
Moreover, security cannot be ‘tacked on’ afterward. Inherently insecure architectures and systems are complicated to fix later on. Instead, security and risk management should be designed from the start, using the enterprise’s business goals to decide on appropriate measures.
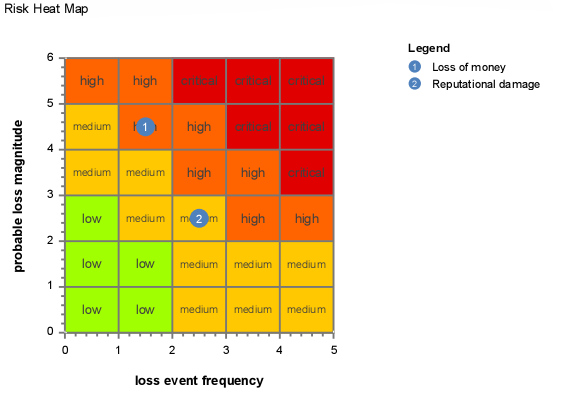
Risk Heatmap
Another common reason for having a mature enterprise architecture practice, especially in heavily regulated sectors such as banking and insurance, is regulatory compliance. Central banks and other regulatory bodies mandate or at least strongly recommend that financial institutions have a well-established enterprise architecture practice, to ensure they are in control of their operation. They may even audit these architectures or use them in other ways to assess the risks the organization runs. Of course, internal auditors, CISO’s, and risk managers benefit from using enterprise architecture artifacts as well. The insights into enterprise-wide relations and dependencies that these provide are important inputs for their tasks.
Implementing standards and policies such as SEPA, Solvency II, Basel III and others requires enterprise-wide coordination, visibility and traceability from boardroom-level decisions on e.g. risk appetite of the organization, down to the implementation of measures and controls in business processes and IT systems. Enterprise architecture as a practice and enterprise architecture models that capture these relations are indispensable to managing the wide-ranging impact of such developments.
To fully benefit from the use of enterprise architecture in the context of security, compliance and risk management, we suggest that you focus on the following:
Managing Consultant & Chief Technology Evangelist at Bizzdesign
Marc contributes to Bizzdesign’s vision, market development, consulting, and coaching on digital business design and enterprise architecture. He also spreads the word on the Open Group’s ArchiMate® standard for enterprise architecture modeling, of which he has been managing the development. His expertise and interests range from enterprise and IT architecture to business process management.