No one is allowed to enter the building without proper authorization; all incoming e-mail messages are filtered; personal computers that are used to store sensitive data do not have a direct connection to the internet, and therefore cannot be accessed remotely. With these enterprise security rules, we have ensured that our private information is safe, right? Wrong!
Cyber-attacks are getting increasingly sophisticated, using a combination of digital, physical and social engineering techniques. A typical example is the so-called “road apple attack”. A would-be intruder “accidentally” leaves a USB flash drive – with company logo – in a public spot such as the company car park. An employee picks it up, and chances are that he will not be able to suppress his curiosity and plug it into his PC. Surprise: the drive is infected with malware which, unless proper measures have been taken, will infect the PC and send sensitive information to the intruder.
Of course, there are several ways to prevent this from happening. The system administrator may decide to completely disable the use of USB drives, but perhaps this is too restrictive, causing employees to find ways to circumvent this. Or perhaps a policy against the use of unverified storage devices suffices, if people are disciplined enough to comply with it… There is no easy way to determine how much security is enough, and how much is too much. In other words, how do we find the optimal position on the trade-off between security, usability and costs?
Most of the present-day security and risk management approaches are based on checklists, heuristics and best practices. Security measures are applied in a bottom-up way, often neglecting the social aspects. This may lead to an overkill of preventive security measures, also in cases where cheaper (and less intrusive) curative measures may suffice. On the other hand, less obvious threats or vulnerabilities in the organization may easily be overlooked.
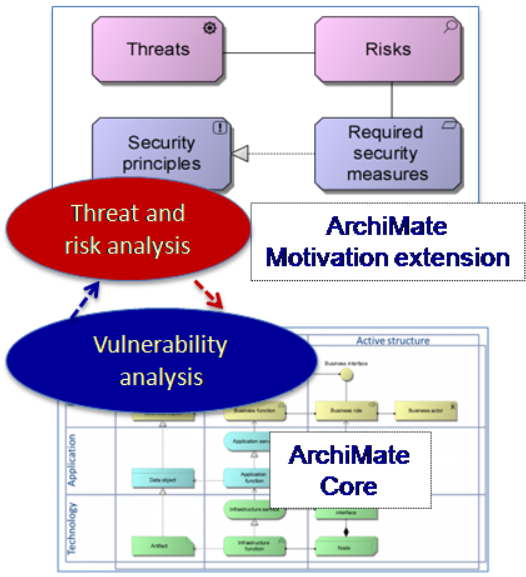
enterprise security management, Archimate core
To avoid this, we advocate a model-based approach to enterprise security management, in which security aspects are fully integrated in the design chain: from strategy and business model, through enterprise architecture, to the design and implementation of the organization and IT support. For this purpose, risk-related concepts are included in existing architecture and design languages. At the enterprise architecture level, ArchiMate, as a broadly accepted open standard (with available tool support) that is suitable to describe business and IT aspects in an integrated way, is an obvious choice. Architectures described in ArchiMate can be linked to goals, principles and requirements, and to detailed design models expressed in languages such as BPMN or UML. The resulting models provide the input for risk and vulnerability analysis, highlighting the areas in the architecture that are most susceptible to attack. In addition, they will guide the design of effective and efficient security measures.
With this approach, BiZZdesign can help you to design a secure organization – without unduly restricting your people in their daily work.