Cybersecurity is one of the key issues the business world has to deal with, and its importance will only rise. As technology steadily evolves to take over increasingly more aspects of business (and personal) life, the need for security is being made pressingly apparent by incidents such as the breaches at Yahoo and Experian, or the WannaCry ransomware attack. Every year, a huge number of companies are hacked. Here are just some of the most famous cases to give you an idea. The result? Countless people worldwide being affected, with the cost of poor cybersecurity easily running in the millions.
When you consider all that, it would then only make sense for an organization to throw everything they’ve got at this problem. Right? Well, though it may sound non-intuitive, the answer is no. The fact is that a company’s ultimate goal is not to be an impenetrable digital fortress but to (deliver value to its customers in order to) stay in business.
This staying in business imperative is actually harder to realize than ever due to how quickly the playing field is changing these days – think technology advancements, changing regulation etc. As such, solely focusing on one aspect of business is a sure recipe for irrelevance. Innovation, service delivery level, customer satisfaction, regulatory compliance, corporate citizenship – these are just some of the other things an organization needs to be mindful of in order to be successful.
Therefore, we believe the best thing for a company that’s serious about its cybersecurity strategy is to operate in a high accuracy, high impact manner. This means acknowledging that blanket measures are doing just as much damage as good, through opportunity cost, user inconvenience, and downright waste. It’s not realistic to expect everything to be 100% secure. There’s a law of diminishing returns at play that ensures you can’t get there, not even if you had all the time and resources in the world at your disposal, which in any case you won’t. So, deliberate action expertly aimed at critical weaknesses is the most reasonable path – that’s why a high accuracy, high impact mindset is key.
Understand the context
To be able to operate ‘surgically’ you first need to have a clear image of the current capabilities. Our collaborative business design platform, HoriZZon, together with its modeling environment, Enterprise Studio, are perfectly equipped to assist with this. Using our suite, users can build accurate digital models of their business and technology landscapes, they can practice capability-based planning, and link the various capabilities to applications, infrastructure, or processes in order to develop an extensive understanding of their organization. As you can imagine, this enables a security-by-design approach because it allows for the embedding of an enterprise risk and security management process into the actual architecture and design processes of the enterprise.
Apart from the digital modeling capabilities that let you explore all aspects of the enterprise, the platform also helps to foster best practice adherence and security compliance. Horizzon supports a wide range of security standards and frameworks, and offers solid content governance features. Mainstream standards such as ISO/IEC 27001, NIST 800-53, CSA, Open FAIR, SABSA and others provide structure, guidance as well as appropriate metrics for users looking to build up a solid security and risk management practice. Indeed, they provide the perfect methodology for identifying, assessing, and prioritizing security objectives and operations. With best practices and a clear big-picture view of the enterprise (and its ecosystem), you are optimally positioned to start a security risk assessment.
Run a security assessment
Because perfect security is an unachievable goal, the emphasis at this point ought to fall on the most effective way of spending security funds. When analyzing risks, threats, opportunities or performance goals, a risk-based approach offers the structure needed to consistently connect and address overlapping concerns. Developing a risk-aware culture within the organization is a crucial component of a successful enterprise risk management program.
At Bizzdesign our approach to risk and security management combines several open standards. If you’d like to learn more, you can download our How to Improve Cyber Security with EA white paper, but for now suffice it to say that the main steps of this assessment stage are: Analyze vulnerabilities, Assess threats, and Calculate risk.
Our platform empowers security professionals to effectively plan, implement and mature enterprise risk management practices within their enterprise. We have even compiled a comprehensive list of vulnerabilities and threats that will prove useful in during the analysis phase. A straightforward way of running a risk assessment is to use the formula Risk = Value x Probability, whereby a higher risk will require more efforts to mitigate against it. At the end of this stage, you should have a good understanding of the risk landscape your enterprise faces. Here is an example of how we would go about such an analysis using Enterprise Studio, HoriZZon’s modeling environment.
The lower part of the model shows the infrastructure and the asset you want to protect (‘Encrypted payment record’). The upper part shows:
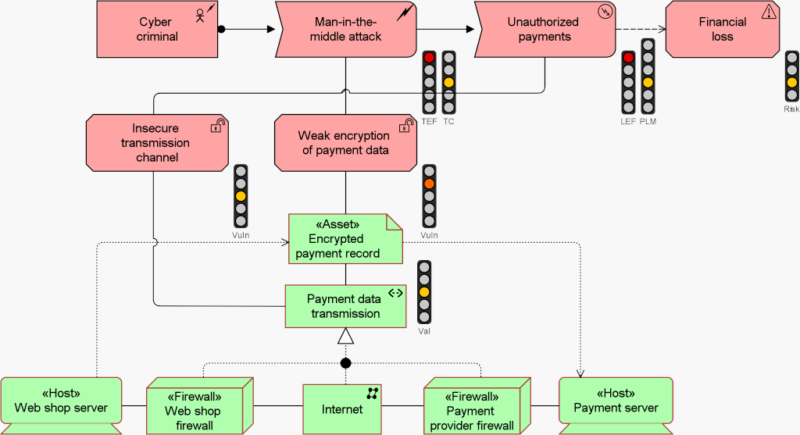
Example of risk analysis
The traffic lights show various parameters, such as the asset value, vulnerability level and the resulting risk level. All these are connected, and our risk analysis algorithm calculates the results, i.e., increasing the risk level if you increase the asset value or threat capability.
Develop and implement risk-mitigating measures
After the assessment stage outline above, the next step is to come up with control measures and deploy them. With an unhindered view of where the weaknesses are, as well as what the consequences of a breach would be, the goal is to devise efficient measures. The structure we recommend is to first consider policies, followed by defining control objectives, then creating control measures, and finally implementing them. Leveraging the enterprise architecture and/or portfolio management output will come in handy again here, because security recommendations can be tied to actual vulnerable elements in the infrastructure layer, for example, or vital business capabilities.
As part of this stage, you should calculate the cost of security measures and compare this with the risks they mitigate. Is that money well-spent? Management is bound to take a report more serious if it is explicit in the benefits that it will deliver. One last recommendation is to relate with decision making figures on a personal level. For instance, you could point to the fact that there is a trend towards personal liability of responsible management in the event of a breach or non-compliant business practice. The EU’s General Data Protection Regulation is one such regulatory framework that is pushing the boundary and piling pressure on not just data processors but also data controllers, who formerly didn’t share any of the responsibility. By steering away from costly blanket measures and attacking the most pressing security issues with precision, an organization stands a better chance of safeguarding against threats but also thriving in the long run.
With companies finding themselves in possession of increasingly more of their customers’ data, and malicious actors doubling up their efforts, cybersecurity is more relevant than ever. Given these circumstances, it’s easy for companies to take an all-out defensive stance and ‘draw the bridge’ on innovation as well as the rest of the elements that contribute towards lasting success. However, this would be a strategic misstep.
That’s because with increased control and prudence you also lower flexibility and agility, which diminishes a business’ overall competitiveness in an era that rewards the ability to adapt quickly. The solution, we believe, is to develop a clear understanding of the enterprise’s risk profile and then develop and deploy mitigating controls in areas that are most at risk. Being able to digitally actualize the enterprise and then run risk assessments on top of real-time models affords great opportunities for improvement.
To learn more about cybersecurity and how enterprise architecture can play a role in creating a solid cybersecurity strategy please download our How to Improve Cyber Security with EA white paper.