Cybersecurity threats are ever increasing. It is sometimes said there are two kinds of organizations: those who know they have been breached, and those who don’t know it yet. To mitigate the risk and damage associated with cybersecurity, it’s important to know how to assess these risks and improve your defenses via security-by-design. It’s also important to plan for what to do if (and when) things do go sideways.
In most organizations, upper-level management awareness of cyber threats has increased due to numerous high-profile incidents over the last few years. The cost associated with ransomware, data breaches and other issues can easily reach in the hundreds of millions.
But sometimes, cybersecurity is still seen as just a technical issue, to be dealt with by the IT director and his or her underlings. One sure way to wake up the boardroom to cybersecurity awareness is regulatory compliance. In these instances, management can be held personally responsible for non-compliance, so there is a strong incentive to take action. New regulation on data privacy, such as the EU GDPR, is only one example where security and privacy concerns have reached the boardroom. Sector-specific and regional regulations, such as the US HIPAA Privacy Rule for the healthcare sector or the NYDFS Cybersecurity Regulation for the financial services sector in New York, are other examples.
But often, management feel like deer in the headlights when it comes to cyber threats. They see the danger but don’t know what to do in the face of these threats. The breadth and depth of these issues may indeed seem incomprehensible and unsolvable. To help management overcome such paralysis, you have to present solutions, not just problems. Enterprise architects are uniquely positioned to contribute to these solutions.
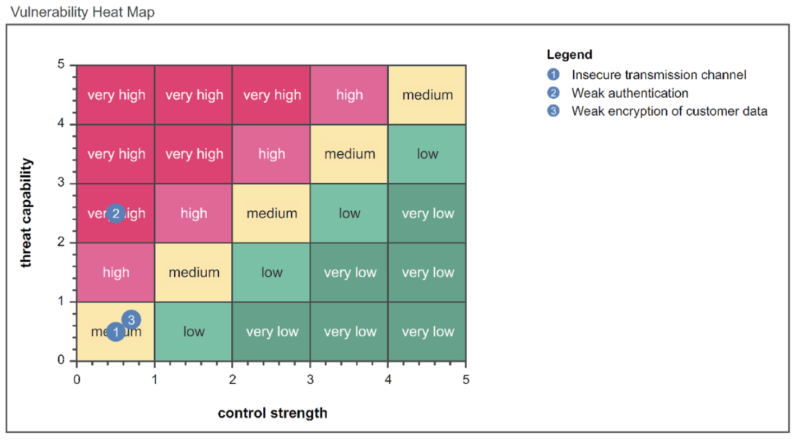
Figure 1: Vulnerability heatmap showing threat levels vs. the strength of controls mitigating against these
As enterprise architects trying to build in cybersecurity processes and standards, you need to involve and inform not just management, but the rest of the organization as well. We have written a series on communicating about information security, discussing information security in the boardroom, providing tips on involving your business and addressing what really works to build security awareness. For more information on how to properly mitigate cyber and information risks, check them out.
To spend your money wisely, you will need to invest in security where it really counts – that is, where it is strategically important. You should, therefore, classify your assets from the perspective of your strategy, taking into account regulatory compliance and other guidelines. What are these assets worth, not just in financial terms but in a broader sense? For example, protecting valuable intellectual property or privacy-sensitive data may be crucial for your business continuity or essential from a regulatory compliance perspective. Such a classification helps you decide on investment priorities and avoid spending too much on relatively unimportant or blanket measures.
Unfortunately, many organizations do not have a clear connection between their strategy and assets. A solid enterprise architecture related to strategic direction and motivation, as well as to implementation within in the organization, provides the “connective tissue” you need. Enterprise Studio provides the integrated support for describing strategy, architecture, processes, systems and data you need to create such a line of sight.
Cyber attacks are becoming increasingly sophisticated, using a combination of digital, physical and social engineering techniques. A common example is the so-called “road apple attack.” A would-be intruder “accidentally” leaves a USB flash drive in a public spot such as the company car park. An employee picks it up, and chances are that he will not be able to suppress his curiosity and plug it into his PC. Surprise: the drive is infected with malware that infects the PC and sends sensitive information to the intruder.
You have to take an integral approach to defend against such attacks, incorporating all aspects of your enterprise, including personnel education, processes and procedures, as well as technical measures like firewalls and antivirus software. Moreover, you should look at this from the perspective of your business goals and strategy, as mentioned before.
With Enterprise Studio, you can capture and visualize various risk and security aspects of your organization. It helps you visualize hazards, risks and mitigation measures in relation to your overall architecture, business strategy and assets so you can perform a true strategy- and value-based risk and compliance assessment. You can measure and visualize the potential impact of these risks and use these insights to prioritize investments in mitigating measures as part of the next step. We have also written about security and compliance analyses in the past if you are seeking more guidance in that area.
Vulnerabilities should not be fixed after the fact, especially not by just slapping on some ad-hoc security measures like an extra firewall. Rather than defining a separate security architecture, you should develop a secure architecture and address risks proactively in the architecture and design across all levels of your enterprise, from people and responsibilities to processes and technology.
You also need to take into account your organization’s position in the broader ecosystem. Having your own house in order may not be enough. For example, if you rely extensively on some external partner, their security may be business-critical for your own operations. Some organizations try to rely on contracts and agreements to take care of this, but that may be insufficient. Legally, you may be held responsible for a breach at, say, an outsourcing partner. Regulation such as the GDPR explicitly states that your organization remains liable for the processing of privacy-sensitive data, even if you hire someone else to do that for you. In some cases, you may even need to have your business partners audited to remain compliant.
In a security-by-design approach, you prioritize investments in security based on the value of your assets and the vulnerabilities you have identified in the previous steps. You calculate the business value and impact of security projects and use this to make a prioritization of IT measures. Use our enterprise portfolio management to decide where to spend your budget most effectively.
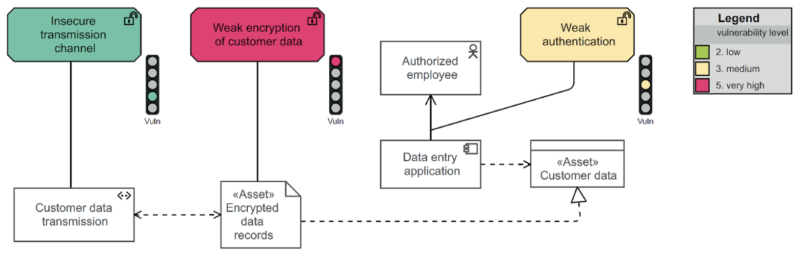
Security-by-design approach
No amount of security measures will make you 100% safe, so you better be prepared to act when things go sideways. Many organizations scramble to find out what to do when they are compromised because they don’t know which parts of the organization or its systems might be affected.
Creating contingency plans based on clear insights into the structure and operations of your enterprise is essential. Up-to-date models of your architecture, processes, systems and data can be a tremendous help in assessing how far a problem could spread, and at which points you should act quickly to limit the impact of a security breach.
But remember Eisenhower’s dictum: “Plans are nothing; planning is everything.” Nothing ever goes completely according to plan, but the development itself of such plans will make clear what you need to know, what the unknowns are and where you have to update your knowledge of your enterprise’s make-up. Connecting Enterprise Studio with systems such as CMDBs, which administer and monitor operational reality, helps to ensure that you use the best and most timely data available.
Finally, all this information needs to be readily accessible for your organization’s “first responders.” BiZZdesign’s HoriZZon portal offers a great solution to this, providing easy-to-use views and dashboards to various types of users, ranging from business decision makers to operational management and people on the proverbial shop floor.
Interested in learning more? Watch on-demand demo or book a demo!