In my previous blog post, I described the new EU General Data Protection Regulation (GDPR) that will go into effect in May 2018, and I outlined its profound effects on organizations, not just in Europe but around the globe. This regulation, and related EU Directives such as the ePrivacy Directive and the Network and Information System Security (NIS) Directive, force organizations to rethink how they deal with personal, privacy-sensitive data. In this blog, I want to address the steps you can take as an architect to help your organization comply with these regulations.
To ensure your organization is compliant, you need a broad overview of how personal data is used and why it was collected, how it is processed, who has access, where it is stored, which third parties are involved, what internal and external threats there are, et cetera. Enterprise architects have a uniquely broad and integrated view of their organization, and have the models and tools at their disposal to assess, improve and assure data protection.
Moreover, the GDPR not only demands compliance, but also requires you to demonstrate compliance. Architecture and architecture models are the major source of this information, in particular when you need a coherent and connected view of everything related to personal data.
View our recorded webinar ‘Don’t let the GDPR be a loose cannon’ and
find out how enterprise architects can leverage architecture models in risk
and security analysis and how Enterprise Studio can help you.
1. In most organizations, enterprise architects do not have final responsibility for ensuring regulatory compliance. This responsibility may lie with your legal department, Chief Risk Officer, Chief Compliance Officer, Chief Information Security Officer, or with the Data Protection Officer newly required by the GDPR. Teaming up with these officials and making them aware of the potential contribution of architecture is the first step.
2. Any work in ensuring compliance will rely on a good overview of the personal data involved. Creating a ‘privacy inventory’ is crucial:
a. Identify all data that counts as ‘personal’ according to the GDPR.
b. Classify this data with respect to its privacy-sensitivity. Make this a part of your regular security processes, where you assign other information security attributes such as the familiar ‘CIA’ (confidentiality, integrity, availability) to your data.
c. Describe the purpose for which this data was collected, and ensure you have (or obtain) the consent of the data subjects to use it in that way.
d. Pay extra attention to special categories of personal data, such as data related to health, biometrics, politics, religion, ethnicity or trade union membership. Use of that data is explicitly prohibited by the GDPR, unless very specific circumstances apply.
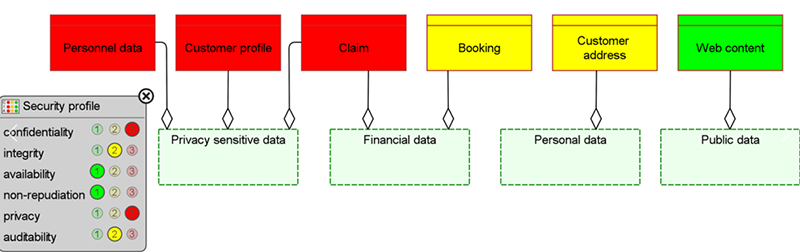
Figure 1. Data classification example, colors based on privacy-sensitivity
3. Analyze the use of personal data, and if possible, leverage your existing architecture models to provide a backbone for your analysis:
a. Start with high-risk areas and the most sensitive types of data. Where is it stored and used?
b. Model data flows: Which applications, processes, people and parties use this data, at which locations, for which purpose?
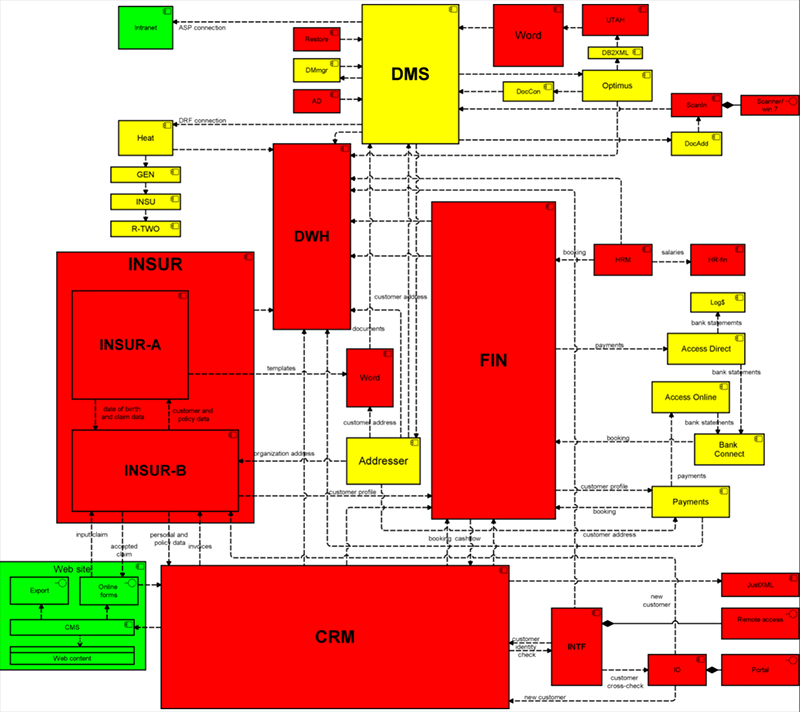
Figure 2. Application landscape with colors based on privacy classification of data used
4. Assess risks to sensitive data, in particular concerning the rights and freedoms of data subjects:
a. Where in your business and IT landscape do you see vulnerabilities?
b. What are common threats that could exploit these vulnerabilities?
c. What are the potential consequences?
You can use the Enterprise Risk and Security Management functionality of Enterprise Studio for advanced analyses of risks, which is based on the ArchiMate and Open FAIR standards of The Open Group. The heatmaps below are an example of the kind of output this can create. BiZZdesign provides is customers with pre-populated content containing common information security and business continuity threats, and the controls prescribed by the ISO/IEC 27001 standard. This gives you a useful starting point, so you don’t have to reinvent the wheel.
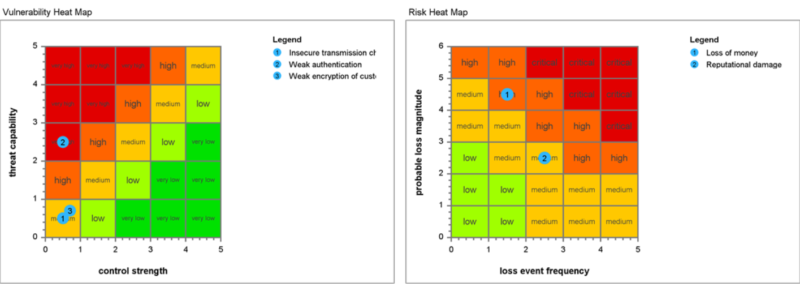
Figure 3. Risk assessment heatmaps
5. Define controls and mitigating measures. Use common standards such as the ISO/IEC 27001 as a basis for identifying useful controls. Importantly, you want to do this as early as possible in a design or change trajectory, to promote a data-protection-by-design approach (which is explicitly mentioned by the GDPR!) and to avoid bolting on measures in a late stage, with all the associated rework, cost and risk.
6. Prioritize risks, allocate budgets and plan the requisite changes and improvements:
a. Evaluate the cost of measures against the risks (the expected loss) to focus your budget on where it really counts.
b. Integrate this decision-making with your overall portfolio management and roadmaps. For example, you may avoid spending too much on fixing up an application that will be phased out soon, and you can combine security-related improvements with other changes.
Enterprise Studio’s Portfolio Management functionality is very helpful in this stage. Clear dashboards help management to decide on priorities and investments, taking all angles into account and allowing you to filter and focus on the essentials (see below).
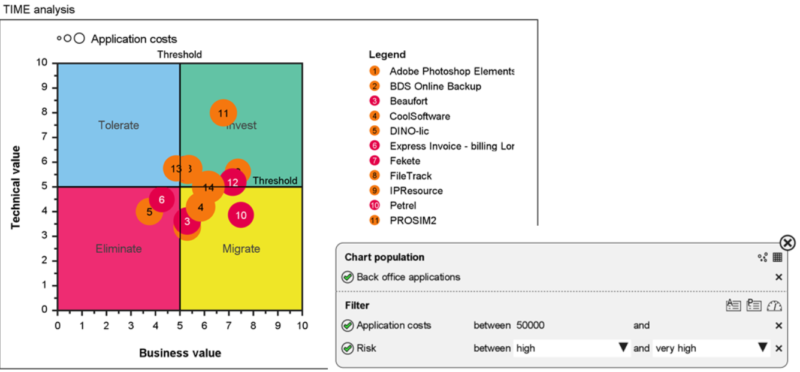
Figure 4. Application portfolio lifecycle chart, filtered for high-risk, high-cost applications
7. Implement the controls and measures you have defined in your organization, processes and systems, and test their security. This is of course what counts most!
8. Demonstrate compliance to the regulatory authorities, showing how you process personal data, how you deal with risks, and which mitigation measures you have implemented.
Of course, this is not a one-shot approach; you should regularly revisit the steps above to ensure you remain compliant and embed this in your governance framework. These steps are also particularly relevant when you perform a Data Protection Impact Assessment (DPIA), which is required by the GDPR for any implementation of a new system that uses personal data.
The BiZZdesign solution helps you to leverage existing architecture and portfolio models and data, to give you a flying start to improve your data security and ensure regulatory compliance. Our integrated approach helps you invest in security where it counts and avoid the penalties and reputational risk of non-compliance, or worse, of a data breach. May 2018 is closer than you think, and a lot of work may be needed, so don’t hesitate and start today!