Protect Your Enterprise: Analyze Your Security With Architecture Models
In a previous blog on cybersecurity, I wrote about the essential steps to keep your organization safe in an increasingly dangerous digital environment:
- Ensure enterprise-wide awareness
- Align security and risk management with business strategy
- Analyze your vulnerabilities and risks
- Take a security-by-design approach
- Assume you are compromised
In this blog, I’d like to zoom in on which instruments to use to help you achieve cybersecurity — in particular for Steps 3 and 4.
Models for cybersecurity
It won’t surprise you that we advocate a model-based approach to analyzing and mitigating cyber risks. Clear, formalized descriptions of your enterprise will help you gain the understanding necessary to provide optimal security solutions. Of course, absolute security cannot be achieved; rather, you should focus on where you need to invest from the perspective of 1) the value of the assets you want to protect and 2) the vulnerabilities associated with these assets.
Our approach to enterprise risk and security management is based on several open standards, most notably the ArchiMate standard for enterprise architecture modeling, as well as the Open FAIR standard for information risk management. More details are described in The Open Group’s white paper on modeling enterprise risk management and security.
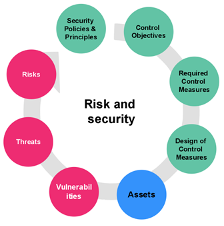
The figure above shows the main steps of our approach, which are built into Bizzdesign Enterprise Studio’s Governance, Risk & Compliance functionality. At the bottom of this figure, you’ll see the assets you want to protect from cyber risks, while at the top we see the policies, principles and objectives that direct the organization. In between are the steps that connect these; on the left side (in red), you’ll see the analysis of cyber risk in your organization, and on the right side (in green) you’ll see the implementation of controls to improve your security. These are the steps of risk and security management:
- Review assets. What are the most important assets that are critical to your enterprise? What do applicable regulations say about these assets? For example, the personal data of your customers may be one such asset. Your reputation as a trustworthy organization may be another. Can you put a value to these elements? That will help you later on when deciding what is most important to protect.
- Analyze vulnerabilities. In what ways are your enterprise’s assets vulnerable? In cybersecurity, “zero-day vulnerabilities,” which are not known to anyone but the attacker, are of course the most dangerous and will naturally not show up in this list. But other vulnerabilities you can recognize should be investigated and linked to the assets they expose. You can reuse the models of your business and IT architecture, possibly augmenting them with relevant security aspects.
- Assess threats. After you assess your asset-specific vulnerabilities, you need to assess whether these vulnerabilities could actually be exploited by so-called “threat events” and “threat agents.” These can range from malicious hackers to hostile governments, as well as your own staff, technical malfunctions, natural disasters and other accidents. We have collected an extensive model of hundreds of common vulnerabilities, threat agents and threat events, which can serve as a starting point for your analysis in this and the previous step.
- Calculate risk. Based on potential threats and the value of your assets, you can assess the risks your enterprise actually faces. In a simple formula, risk = value x probability, the higher the risk, the more you will want to invest in mitigating against it. The figure below shows an example of such an analysis, gradually built up in these first four steps.
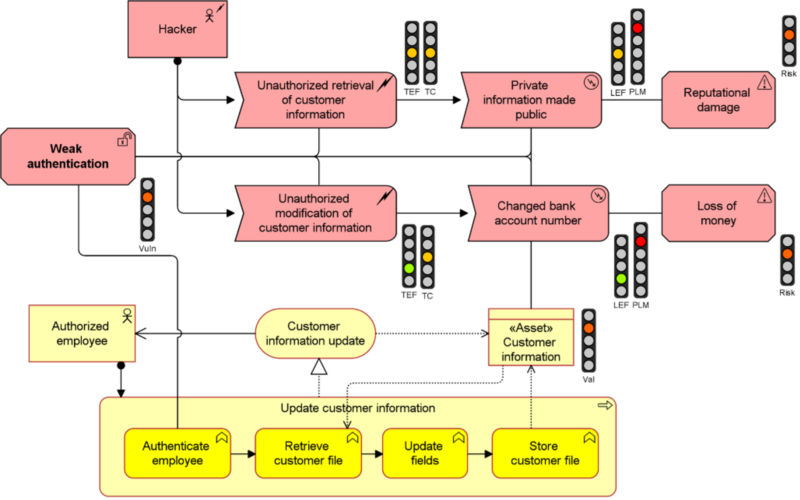
The lower, yellow part of the model shows the business process and the asset to be protected (‘Customer information’). The upper part shows, from left to right:
- The vulnerability (‘Weak authentication’)
- The threat agent (the hacker)
- Threat events
- Potential loss events resulting from these threats
- The resulting risks
The traffic lights show various parameters, such as the asset value, vulnerability level and the resulting risk level. All these are interconnected and our risk analysis algorithm calculates the results, e.g. increasing the risk level if you increase the asset value or threat capability.
- Create policies. To deal proactively with potential cyber risks, you should define appropriate security policies and principles that are in line with your business strategy and also follow applicable regulations. This may, for example, include principles such as security-by-design, separation of duties, restricted access to personal data and other common policies. Regulatory frameworks like the GDPR require solid data protection policies, with hefty fines for non-compliance and even personal liability of responsible management. This, in turn, influences the value of the assets you want to protect. It’s not just their intrinsic value at stake; fines, reputational damage and other side effects should also be taken into account.
- Define control objectives. Based on the policies you created in the last step, you should now define appropriate control objectives. One standard approach, for example, is to classify the confidentiality, integrity, availability, privacy-sensitivity and other attributes of your data, according to common use cases you have. For example, data on your website will need low confidentiality but high availability, whereas customer data will have much higher privacy and confidentiality requirements, while availability might be less of a concern.
- Create control measures. These control objectives are then translated into applicable control measures, which tell you what to do to reach these objectives. Relevant standards, such as ISO/IEC 27001, NIST 800-53, CSA and others may help by providing a predefined and well-organized set of control measures. Below, you see a small excerpt from a model of the ISO/IEC 27001 standard, showing one specific control objective and a number of related control measures, expressed in the risk and security overlay of ArchiMate that is defined in the Open Group whitepaper mentioned above.
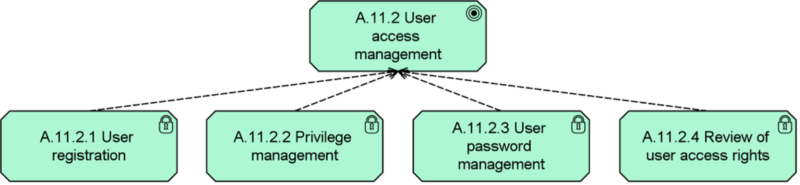
The strength of these control measures can also be used as input in the risk calculations shown in the previous figure. The stronger your controls, the lower your vulnerabilities, and, therefore, the lower risks you run.
- . The final step is to design the implementation of these control measures as part of your own architecture, processes and systems. For example, you’ll need to figure out how you perform user registration (the first measure from the previous figure). The cost of implementing these measures can be compared with the risks you run. Are they really worth it, or are you protecting low-value assets with overly expensive controls?
The analysis shown above is, of course, something to be done by modeling and risk assessment experts, and may look complicated to the uninitiated. The outcomes, however, can be presented in user-friendly heatmaps like the one below.
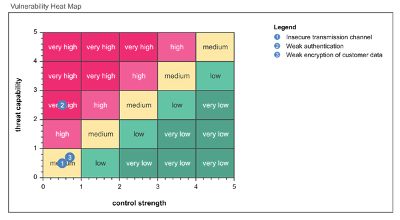
The heatmap above shows how high capability of threats (e.g. smart hackers) combined with low strength of controls results in a very high vulnerability level. The other two vulnerabilities in this heatmap are probably less urgent.
This analysis helps management prioritize investments in improving security like, in this example, implementing rules on password length or instituting multi-factor authentication. Thus, your organization has room in its budget to invest where it really counts.
Security architecture is a continuous concern
Risk management is a continuous, iterative process. The process outlined above should be run regularly to assess new vulnerabilities and threats and to keep your policies, principles and controls updated with your organization’s strategy and applicable regulatory demands. Moreover, the fact that you have such a risk management process is, in itself, demanded by various regulatory frameworks.
Embedding this within your regular architecture and design processes provides you with a security-by-design approach — a much more effective way to improve your organization’s resilience than simply tacking on some security measures after a cybersecurity event.
There is no guarantee that nothing will ever go wrong. Nevertheless, having such a model-based approach to risk analysis and mitigation will prove to be a great investment in your organization’s cybersecurity, business continuity and resilience where (and when) it really counts.
Interested in learning more? Contact one of our experts for a demonstration!



